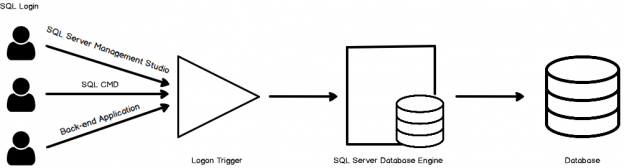
This article contains the SQL Server login Authentication scope on the Security side. We will find the subtleties, how Login Authentication extension can be controlled SQL Server level Logon trigger.
Common SQL Server Principals are clients and Logins and that is constrained by authorizations with GRANT and DENY. SQL Server database engine will authorize the login by authentication request from any Query Management Studio(SSMS), Application Integration or some other apparatuses.
Development, QA or stage servers are fine to permit all login to Authenticate SQL Server utilizing diverse customer applications yet for Production servers, we can’t. SQL Server Logins ought to be limited with an entrance approach to authorized authentication for Client Applications. In this article, we will experience in detail to confine the SQL Server login scope with predefined rules for the approval of customer’s / client applications.
Essentially, Database Engineers will have the consented access to utilize the SQL Server database engine as a level of Designation. As the Industrial standard, organization will make individual login for database users to get to access on production; Now, each application could have diverse SQL login so as to communicate with a database, be that as it may, the SQL login ought to be authorized by the database engine utilizing customers\client application just and not just by utilizing any Query management studio or tools.
The various types of SQL triggers, for example, DDL(Data Definition Language), DML(Data Manipulation Language) and Logon triggers are upheld by Microsoft SQL Server.
Authorization rule metrics can be defined in Logon trigger to command over SQL login to Enhance the Security of the Database. See here, we have attempted to clarify various situations having been connected different rationales in Logon trigger with a model:

We are to give a shot with the logon triggers such that it would make a hazard to the trigger ought not to follow up on as likely it ought to and it would not allow finishing the login procedure on the SQL server. See here, to improve security, in this kind of situation the Database administrator ought to be reached so as to determine the issue and to have the option to reconnect to the SQL Server by altering or dropping the Logon trigger.
Allow Logins to Authorize to access database Engine.
In specific situations, user-defined Windows and SQL logins exist in SQL Server instance; be that as it may, for security reasons, we just utilize a couple of user accounts using the back-end applications. Prudently this sort of excess logins ought to be removed.
Recommendation: We should plan our framework such that the users ought to have the option to interface legitimately to the database and hence to limit to control their permissions, to avoid any complication to trigger and increase the security of the database.
For example, four Logins are existed in server “sa”, “jraiyani”, “myel” and “sdonda”. As a necessity, we have to permit just a couple of them “sa” and “jraiyani” to the access to SQL Server database engine, at that point below trigger assistance us to oversee it.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
CREATE TRIGGER Prevent_login ON ALL SERVER WITH EXECUTE AS 'sa' FOR LOGON AS BEGIN DECLARE @LoginName sysname DECLARE @LoginType sysname SET @LoginName = ORIGINAL_LOGIN() IF(@LoginName NOT IN ('sa', 'jraiyani')) BEGIN ROLLBACK; --Disconnect the session END END |
On the off chance that the user is attempting to log in with the restricted Login, at that point SQL Server will return a blunder as Logon failed for log in because of trigger execution. We can see the equivalent in the below screen capture.

The SQL Server is intended to deal with tremendous quantities of speedy login endeavours, thusly for the reason of security, exceptionally suggested that sa login is required to disable in SQL Server.
At the point when the users get allowed to access the confined information that is the place, the client triggers the most minimal at the security standard.
Allow certain Applications to Authorize to access database Engine.
There is no security competency that will enable any authorized Login to associate from any program (for example Back-end Application), however no other than it, for example, Query Management studio or different applications.
You may discover interesting as a workaround is to utilize logon triggers to attempt to maintain a strategic distance from accidental access through non-approved or non-authorized programs. In any case, be cautioned: This isn’t a security limit, and it is anything but difficult to sidestep, however it will enable you to keep fair individuals genuine. So I will make a logon trigger that will check the application name on the session, and square any application which hasn’t affirmed for this Login.
See here, this trigger would impact every one of the users, subsequently to avoid redundant restrictions on a specific type of Login. Subsequently we have added the checks to stay away from preventable restrictions on specific segment of Login, as and when a user group attempt to connect with SQL Server, the security Logon trigger will check the name of the application and the login trigger will raise the blunder message “Connection to fail” on the off chance that the login qualifications do not match.
the Login who is authorized will most likely get to the Database by avoiding the security triggers and the unauthorized Login won’t ready to deny that she/he attempted to sidestep your policy.
In below example, we allowed ‘myel’ user to login in using ‘SQLCMD’ application only.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
CREATE TRIGGER Prevent_login ON ALL SERVER WITH EXECUTE AS 'sa' FOR LOGON AS BEGIN DECLARE @AppName varchar(max) DECLARE @LoginName sysname DECLARE @LoginType sysname SET @AppName = APP_NAME() SET @LoginName = ORIGINAL_LOGIN() IF(@LoginName = 'myel' AND @AppName like 'SQLCMD') BEGIN RETURN;--Login Authorized END IF(@LoginName NOT IN ('sa', 'jraiyani', 'sdonda')) BEGIN ROLLBACK; --Disconnect the session END |
User logged in successfully for authorized SQL Login.

SQL Server will not allow restricted user which has been mentioned in second IF condition. In that case, SQL Server will return error with Logon trigger reference as below image.

We can mention here different client application name and combination of the client application and SQL Login name to get the filter out in SQL Authentication.
The firewall will be continually denying any unauthorized correspondence and verifying the Database server behind it. The firewall won’t permit any immediate client to get separated from the correspondence from the particular applications. The change principle control methods are prepared by Firewall and the System Manager and Database Administrator could get the notice as a warning of standard changes can be set.
Allow Login from Authorized Machine IPs Only
The Microsoft SQL Server has got an inbuilt function for trigger called EVENTDATA() that would return Login event data in XML format for Logon event. However various kind of rules can be configured with EVENTDATA() that would allow certain authorized IP address only to authenticate by the Database engine. In most cases, a database server is accessible by the application server and responsible Database Engineer only and those users who are able to access SQL Server Instance using internet or Intranet.
Various Security Layers applied by organizations to connect SQL Server Instance. For Example, VPN (Virtual Private Connection), Port access, SQL connection. These IP restrictions can be incorporated with the firewall as well. However here are a few described Logon trigger rules with an example to allow authorized IP addresses only. EVENTDATA() returns below XML with connection data while Logon trigger executed.
|
1 2 3 4 5 6 7 8 9 10 11 |
<EVENT_INSTANCE> <EventType>LOGON</EventType> <PostTime>2019-09-03T12:33:59.773</PostTime> <SPID>53</SPID> <ServerName>JERRY\JIGNESH</ServerName> <LoginName>sa</LoginName> <LoginType>SQL Login</LoginType> <SID>AQ==</SID> <ClientHost>192.168.1.1</ClientHost> <IsPooled>0</IsPooled> </EVENT_INSTANCE> |
To get Client host address use below XML query in Trigger only. Because, In regular session of SQL Server, it will return NULL value.
|
1 |
EVENTDATA().value('(/EVENT_INSTANCE/ClientHost)[1]','nvarchar(128)') |
To apply this rule on logon trigger, needed to prepare a list of authorized IP address and add the list to the trigger with applying filter. Below example help us to design rule to allow a particular IP list on Logon. we can add “<local machine>” in the IP whitelist to allow localhost connection.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
CREATE TRIGGER prevent_ip ON ALL SERVER WITH EXECUTE AS 'sa' FOR LOGON AS BEGIN IF (EVENTDATA().value('(/EVENT_INSTANCE/ClientHost)[1]','nvarchar(128)') IN ('192.168.1.1', '192.168.1.1', '<local machine>')) BEGIN RETURN; -- Login Authorized END ELSE BEGIN ROLLBACK; -- Disconnect the session END END |
In the above illustration, if requesting client application IP address is valid as IP whitelist then Logon trigger will allow to access database engine or else Login request will be kicked out with an error message. Now to make a combination of multiple rules within trigger we can define our own logic. Different Logon triggers are additionally bolstered in the single SQL Server instance.
Conclusion:
With the assistance of the Logon trigger, the client connections can be likewise be observed, similar to Which client got associated and when the connection was built up in a joint effort with the guidelines require at different SQL Server security levels. There are regular possibly high-security arrangement rejections, for example, default organize settings, logins, and passwords as often as possible utilized by aggressors.
Table of contents
| Limit SQL Server Login Authentication scope using a Logon Trigger |
| Database Level DDL Triggers on Tables |
| Database Level DDL Triggers for Views, Procedures and Functions |
See more
Interested in an enterprise-level SQL Server audit and compliance solution for GDPR, HIPAA, PCI and more, including tamper-proof repository, fail-over/fault tolerant auditing, tamper-evident repository, sophisticated filters, alerting and reports? Consider ApexSQL Audit, a database auditing tool for SQL Server

- Page Life Expectancy (PLE) in SQL Server - July 17, 2020
- How to automate Table Partitioning in SQL Server - July 7, 2020
- Configuring SQL Server Always On Availability Groups on AWS EC2 - July 6, 2020