This article speaks to, how to copy SQL Logins on the new server with Server Level roles and database-level permissions as existing Source to Destination SQL Server instance using a script.
Every rendition of SQL Server has distinctive security highlights, as does every form of Windows, with later forms having improved usefulness over before ones. Understand that security includes alone can’t ensure a protected database application. Database Administrator plays out the errand to Move or Copy SQL Logins when a new server is going to an arrangement on any environment (Development\ Testing \Staging or Production) or presenting the new database on any of the environment.
Microsoft SQL Server gives the user and role-based security. Server predefined role with a group of permissions will be appointed to the user rather than individual permission and this arrangement of permissions of SQL Server roles can’t be changed. Every role will have recognized authorizations (permissions) and extent of access to the SQL Server and its databases.
Each SQL login of SQL Server can be doled out to SQL Server roles in database security. indeed, even we can utilize user characterized roles also with the number of principle consents as required. fundamentally, we have three sorts of login in SQL Server, for example, Windows Login, SQL Logins and Windows Group Login (Active Directory).
A user could have Grant or Deny for various object types, thusly we can create a script to give permissions to access objects to the users on another server. As a feature of database security, we ought not to give full access to everybody. along these lines, we bifurcate the user’s permissions with the SQL Logins to the assigned individual. For every database, we ought to have several SQL logins with various object-level authorizations.
In a schedule, we can enable the current users to have permissions to access on recently made database or we can adjust the authorizations or permission on the existing arrangement with the utilization of GRANT and DENNY articulations. In any case, if there should be an occurrence of server relocation or Hardware refreshment action, the permissions set ought to be foreordained with the number of permissions as best rehearses.
How to Copy or Move Logins?
Generate script at Source Server and execute at Destination with 3 errands.
- Create SQL Logins
- Assign Server role to the SQL login
- Create User at Database Level with object permissions
CREATE SQL Logins
Below query will create all logins with a password that exist on SQL Server Instance. It ought to be executed on the source server.
sys.sql_logins incorporates SQL Server inside service level users and System Administrator. So we can bar those users in the script while setting it up for SQL Server migrate logins.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
SELECT 'IF (SUSER_ID('+QUOTENAME(SP.name,'''')+') IS NULL) BEGIN CREATE LOGIN ' +QUOTENAME(SP.name)+ CASE WHEN SP.type_desc = 'SQL_LOGIN' THEN ' WITH PASSWORD = ' +CONVERT(NVARCHAR(MAX),SL.password_hash,1)+ ' HASHED, CHECK_EXPIRATION = ' + CASE WHEN SL.is_expiration_checked = 1 THEN 'ON' ELSE 'OFF' END +', CHECK_POLICY = ' +CASE WHEN SL.is_policy_checked = 1 THEN 'ON,' ELSE 'OFF,' END ELSE ' FROM WINDOWS WITH' END +' DEFAULT_DATABASE=[' +SP.default_database_name+ '], DEFAULT_LANGUAGE=[' +SP.default_language_name+ '] END;' COLLATE SQL_Latin1_General_CP1_CI_AS AS [-- Logins To Be Created --] FROM sys.server_principals AS SP LEFT JOIN sys.sql_logins AS SL ON SP.principal_id = SL.principal_id WHERE SP.type IN ('S','G','U') AND SP.name NOT LIKE '##%##' AND SP.name NOT LIKE 'NT AUTHORITY%' AND SP.name NOT LIKE 'NT SERVICE%' AND SP.name <> ('sa') AND SP.name <> 'distributor_admin' |
See here, you can see the number of logins with hash organized password. T-SQL query will create the script for Windows logins and SQL Logins for SQL Server migrate logins. To reject the Windows Login, we can apply the filter on sp.type section by including SP.type <> ‘U’ in the above SQL explanation.
Execute the outcome set of above articulation at goal server and check those new logins are readied or not utilizing sys.sql_logins DMV. Now, logins are copied however roles that are mapped in the source server that won’t be integrated with SQL logins at the Destination Server.
Assign Server role to the login
Server roles are kept up by the Database Engineer or Administrator and apply to the whole server, not an individual database document. The public role sets the fundamental permission for all users. Each user that is added to SQL Server is consequently relegated to the public role, you don’t have to do anything. Database roles are connected to an individual database as part of security.
Each login can have a distinctive roles and permissions.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
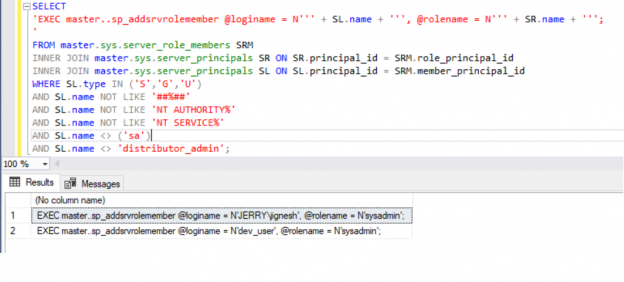
SELECT 'EXEC master..sp_addsrvrolemember @loginame = N''' + SL.name + ''', @rolename = N''' + SR.name + '''; ' AS [-- Roles To Be Assigned --] FROM master.sys.server_role_members SRM INNER JOIN master.sys.server_principals SR ON SR.principal_id = SRM.role_principal_id JOIN master.sys.server_principals SL ON SL.principal_id = SRM.member_principal_id WHERE SL.type IN ('S','G','U') AND SL.name NOT LIKE '##%##' AND SL.name NOT LIKE 'NT AUTHORITY%' AND SL.name NOT LIKE 'NT SERVICE%' AND SL.name <> ('sa') AND SL.name <> 'distributor_admin'; |

On the off chance that the user has not been assigned to any role, it is doled out to ‘Public’ role of course. In the above result, “test_test” client isn’t visible, the fact that they are not allocated to any roles. We can see in below picture.
We have enabled users to associate the SQL Server Instance utilizing the above script. Notwithstanding, for database-level permission, we have to make the user at the database level and relegate the permissions.
Create User and permissions on Database Level
As to control security imperative or to maintain a strategic distance from information harming Attacks and SQL Injection, been appointed to the role isn’t satisfactory at SQL Server. Subsequently, we apply second-level access to the database. Presently to keep it in underline with allotting permissions contingent upon sort of objects. The user ought to be allowed with important benefits just at database level by necessary privileges.
Different kind of Article or Object-level permissions can be incorporated with the users or roles relying upon the prerequisites, which could be DDL and DML level authorizations on schema objects suchlike EXECUTE, SELECT, DELETE, INSERT, ALTER, CONNECT, CONTROL, TAKE OWNERSHIP, VIEW DEFINITION, and so forth. SQL Server characterized roles have some pre-set permissions sets; be that as it may, the worth probably won’t get populated for every one of the roles. The permission gets impacted over the object can be stated by consent types GRANT, DENY, and so on.
Indeed, even inside the schema, we can access controls on different sorts of SQL Server objects, for example, the Tables (System table and User Table), Functions (Scalar Function, Table Valued Function), Views, Procedure and so on. Presently for the Financial information which should be classified, the client ought to have the entrance control on columns of the table also. All member from SQL Server login shouldn’t see the columns of the table where column level permission isn’t permitted. In this manner, when SQL Logins are being moved or copied to the next server for the same database here a similar kind of security get to permissions must be replicated and connected with logins. See here, every one of the cases we saw, we have quite recently replicated Logins and its role to SQL Instances, anyway, those ought to exist on database level too.
Underneath query will create a list of users which are existing in the database. With the end goal of the movement, the query can be executed in a LOOP to get it for all client databases.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
SELECT 'USE '+ DB_NAME()+'; CREATE USER ['+dp.name+'] FOR LOGIN ['+dp.name+'];'+ 'ALTER USER ['+dp.name+'] WITH DEFAULT_SCHEMA=['+dp.default_schema_name+'];' AS [-- Logins To Be Created --] FROM sys.database_principals AS dp INNER JOIN sys.server_principals sp ON dp.sid = sp.sid WHERE (dp.type in ('S','G','U')) AND dp.name NOT LIKE '##%##' AND dp.name NOT LIKE 'NT AUTHORITY%' AND dp.name NOT LIKE 'NT SERVICE%' AND dp.name <> ('sa') AND dp.default_schema_name IS NOT NULL AND dp.name <> 'distributor_admin' AND dp.principal_id > 4 |
With the expanded the size and complex nature of a database, the methodology ends up being increasingly more toilsome to deal with, specifically if attempting to allocate object-level permission to individual logins. The level of difficulty increases, and it is expanding that hitches show up during deployment, the access-control error happens, and security evades show up. This leads unavoidably to the way of least conflict where, for instance, all user accounts end up as members of the db_datawriter and db_datareader roles or, far more atrocious, reasonable access control is completely relinquished for ‘getting the application working’.
The initial phase in ensuring your customer’s information is figuring out which users need to see which information and after that enabling access to just those users. For instance, a finance agent presumably sees compensation figures for everybody in your organization while group directors approach pays rates for colleagues. Singular representatives have no compelling reason to see compensations by any means.
Now, we can generate the number of schema and object permissions for the user using the below query:
The query needs to be executed in each database using a loop. It returns user with individual permission in a separate statement.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
SELECT 'USE '+ DB_NAME()+'; '+CASE WHEN dp.state <> 'W' THEN dp.state_desc ELSE 'GRANT' END +' ' + dp.permission_name + ' TO ' + QUOTENAME(dpg.name) COLLATE database_default + CASE WHEN dp.state <> 'W' THEN '' ELSE ' WITH GRANT OPTION' END +';' AS [-- Permission To Be Assign to the User --] FROM sys.database_permissions AS dp INNER JOIN sys.database_principals AS dpg ON dp.grantee_principal_id = dpg.principal_id WHERE dp.major_id = 0 AND dpg.principal_id > 4 AND (dpg.type in ('S','G','U')) AND dpg.name NOT LIKE '##%##' AND dpg.name NOT LIKE 'NT AUTHORITY%' AND dpg.name NOT LIKE 'NT SERVICE%' AND dpg.name <> ('sa') AND dpg.default_schema_name IS NOT NULL AND dpg.name <> 'distributor_admin' AND dpg.principal_id > 4 ORDER BY dpg.name |

Conclusion
This article is designated to help and structure a legitimate database access control framework and SQL Logins Relocation or Migration utilizing script. counting single content to play out all undertaking, it would assist a great deal with making it simple. For automation, dynamic SQL script keeps running on a remote server to make it brisk.
- Page Life Expectancy (PLE) in SQL Server - July 17, 2020
- How to automate Table Partitioning in SQL Server - July 7, 2020
- Configuring SQL Server Always On Availability Groups on AWS EC2 - July 6, 2020