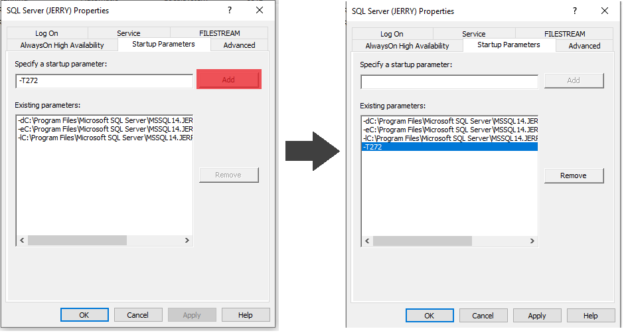
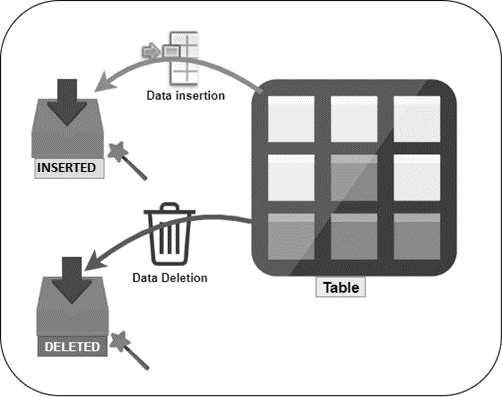
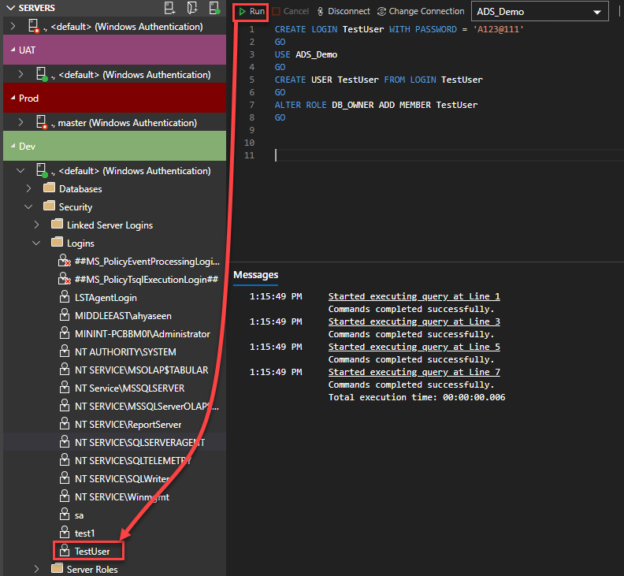
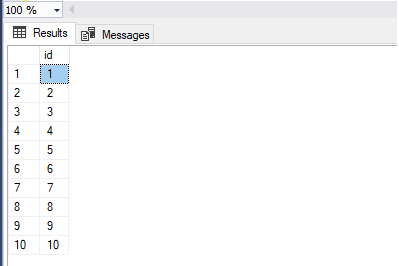
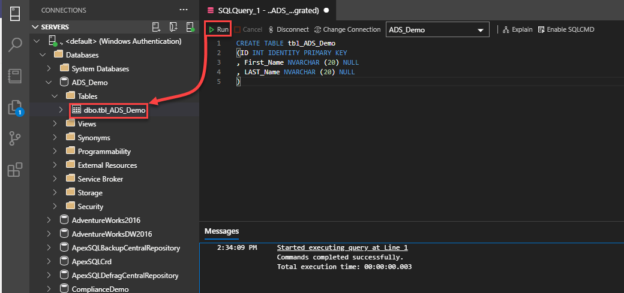
In this article, we will examine the Identity Cache feature and the identity jump issue. Sometimes we see that identity jumps by some specific or random value in the auto-incremental columns, which is known as the identity jump issue. Usually, it occurs when the SQL Server instance is being forced to restart. This skipped gap is particularly depending on the data type of the column, and most of the time, it is possible that column type can be INT, BIGINT, or Numeric.
Read more »