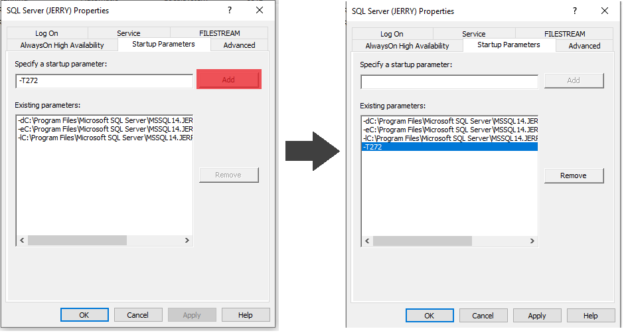
In this article, we will examine the Identity Cache feature and the identity jump issue. Sometimes we see that identity jumps by some specific or random value in the auto-incremental columns, which is known as the identity jump issue. Usually, it occurs when the SQL Server instance is being forced to restart. This skipped gap is particularly depending on the data type of the column, and most of the time, it is possible that column type can be INT, BIGINT, or Numeric.
Read more »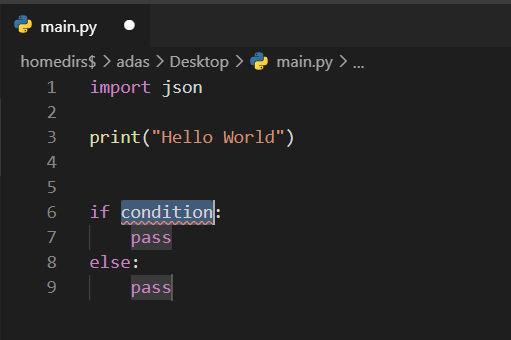
Setting up Visual Studio Code for Python Development
July 1, 2020In this article, I am going to explain how to set up your Visual Studio Code for Python Development. Visual Studio Code or, popularly known as VS Code, is one of the free and open-source code editors developed by Microsoft and is mostly preferred by developers of all the major programming languages due to its flexibility and other integrated development tools like debugging, IntelliSense, etc. Visual Studio Code is available to be downloaded for all the major operating systems like Windows, Linux, and macOS. You can visit https://visualstudio.microsoft.com/ to download it based on the OS you are using.
Read more »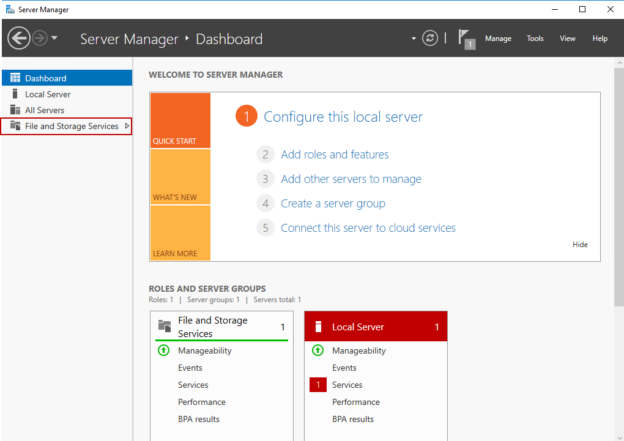
Installing and configuring a iSCSI Target Server on Windows Server 2016
June 30, 2020In this article, I am going to explain how we can install and configure the iSCSI Target Server Role on Windows Server 2016. iSCSI stands for Internet Small Computer System Interface and iSCSI Target Server allows you to boot multiple computers from a single operating system (OS) image.
Read more »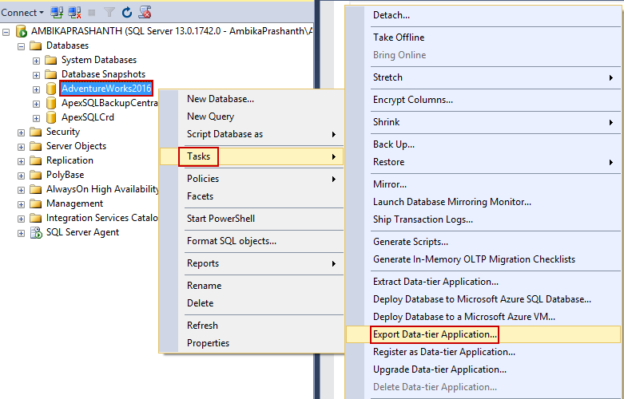
Migrate an on-premises SQL Server database to an Azure SQL database
June 30, 2020In this article, we will discuss and understand a method to migrate an on-premises SQL Server database to the Azure SQL database.
Read more »
The SQL Server Assessment Extension for Azure Data Studio
June 30, 2020Azure Data Studio extensions enable adding new functionality for development and administrative tasks. It is an open-source functionality and allows Microsoft as well as third party extensions using Marketplace. We explored a few useful extensions in the Azure Data Studio category of articles.
Read more »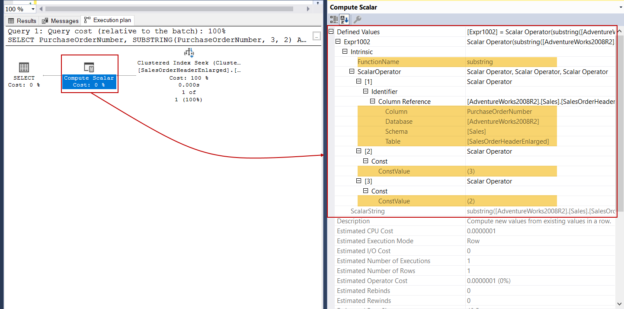
SQL SUBSTRING function and its performance tips
June 30, 2020In this article, we will briefly explain the SUBSTRING function and then focus on performance tips about it.
Read more »
Different ways to search for objects in SQL databases
June 29, 2020This article explores various ways to search for database objects in SQL database such as tables, stored procedures, functions, and views.
Read more »
SQL Server Connectivity Interview Questions & Answers for SQL Server Database Administrators
June 29, 2020In this article, we will discuss a number of questions that you may be asked while being interviewed for a SQL Server Database Administrator (DBA) position. These questions will concentrate on the SQL Server connectivity concept, components, configurations, and troubleshooting.
Read more »
AWS Launch Wizard for quick SQL Server Always On deployments
June 29, 2020SQL Server Always On is a high-availability and disaster recovery solution. We can use multiple secondary replicas for configuring database backups, redirect read requests to offload primary instance load.
Read more »
Migrating your data into Azure Cosmos DB
June 26, 2020In the previous article, Start your journey with Azure Cosmos DB, we provided you with the backpack that helps you to start your journey with Azure Cosmos DB and filled it with detailed information about the Cosmos DB usage benefits, how to create your first Cosmos DB account, create a new database, container, and items and finally how to query the data stored in that container.
Read more »Data Masking or Altering Behavioral Information
June 26, 2020As tracking behavioral data becomes increasingly popular, firms may overlook areas where they can collect the same information while data masking details that can be used in a compromise. Behavioral data collection can be extremely dangerous as it allows attackers a wide range of attacks, from spoofing targets to automating custom attacks on targets. Since behavior can reveal key details about us, this information may be as costly as private identifiable information. When tracking behavioral data, we want to weigh risks, and, in some cases, we can accomplish the same result without specific details. In other cases, we may want to mask specific behavioral information on reports that are generated, even if we retain the specific time. We’ll look at a method where we can accomplish either – updating data to remove time or data masking specific time while returning the information we want.
Read more »
Getting started with Azure Function Apps
June 25, 2020In this article, I am going to explain how to get started with Azure Function Apps. In my previous article, An introduction to Serverless Applications, I have mentioned the serverless architecture and the various cloud offerings to develop serverless applications. As we know, in serverless architecture, the users only write the business logic code, and all other worries are taken care of by the cloud provider. This helps businesses to quickly implement solutions and ship it to customers with more quality. Also, another important point about serverless applications is that they are scalable on-demand, which means as a developer, we no longer need to monitor or manually pull up the resources when the executions are more.
Read more »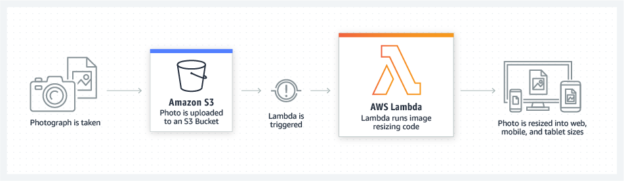
An introduction to Serverless Applications
June 25, 2020In this article, I am going to describe what are serverless applications and how are these developed. I will also introduce the concepts of serverless computing and how to deploy one using Azure Functions. This article is targeted towards most of the data professionals who want to gain some basic knowledge of serverless applications and the underlying architecture and cloud computing. In recent times, cloud computing has become one of the most important domains for many big organizations and it has thus become essential for all to have some basic information on the same.
Read more »
Using the SSIS Script Component as a Data Source
June 25, 2020Introduction
SSIS Script component is one data transformation tasks in SQL Server Integration Services (SSIS). SSIS is an integration tool in the Microsoft BI family to extract data from heterogeneous data sources and transform it to your need. Apart from the standard data sources such as databases, text files, excel files, and web services, there can be instances where you need to retrieve non-traditional data sources. For example, let us say you want to extract the details of text files such as file sizes, created date, etc. In these types of scenarios, traditional data sources cannot be used.
Read more »
It is time to specify your Microsoft Certifications path
June 24, 2020In this article, we will discuss all Microsoft Certifications paths in a way that helps you to drive on the correct road, to meet the requirements of the current job career growth or the job that you plan for.
Read more »
Digging deeper into Azure Data Studio: Extensions and Azure SQL DB Development
June 24, 2020In the previous articles listed below, we went through the Azure Data Studio tool, starting from the installation procedure, showing the purpose of each component, how to organize your connections, and develop the different types of SQL Server database objects using the interactive query editor in that data studio.
Read more »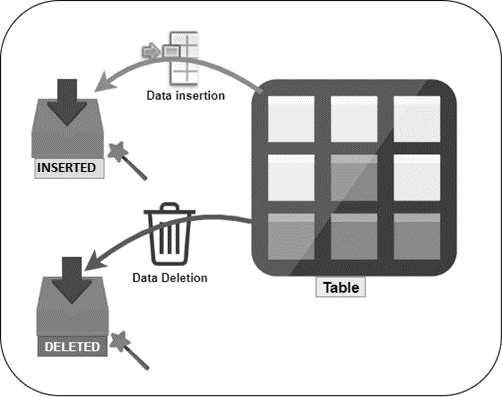
Magic Tables in SQL Server
June 23, 2020There are Magic Tables (virtual tables) in SQL Server that hold the temporal information of recently inserted and recently deleted data in the virtual table. INSERTED and DELETED are two types of magic tables in SQL Server. An INSERTED magic table is populated with INSERT and UPDATE operations and DELETED magic table is populated with UPDATE and DELETE operations.
Read more »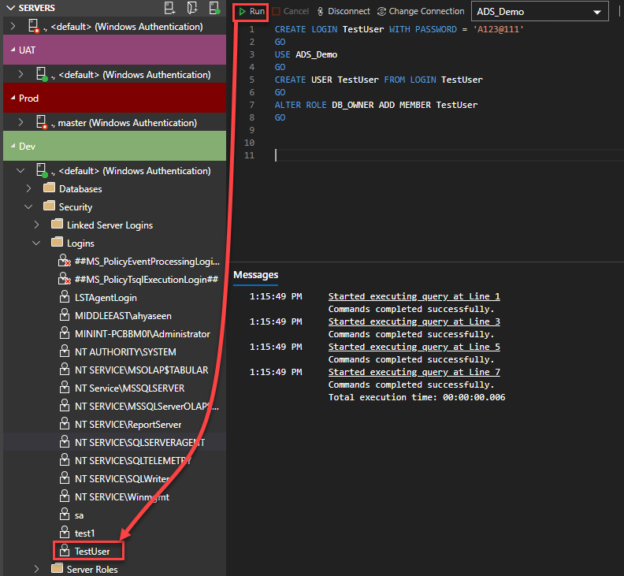
Digging deeper into Azure Data Studio: More code and less GUI
June 23, 2020In the previous two articles, Starting your journey with Azure Data Studio and Developing your SQL Server database using Azure Data Studio, we introduced the Azure Data Studio tool by describing the main components of that data studio and showed how we can take advantages from it in developing and organizing the database related projects.
Read more »
Execute a SQL Server procedure inside a function
June 23, 2020In this article, we will ensure that the execution of the SQL Server procedure inside the function is possible. A common understanding of the database developer is that the procedure cannot be utilized or executed inside a user-defined function because the user-defined function does not allow performing DML operation with the table. The procedure is allowed to play with the database and its property, whether a user-defined function isn’t. That should be the essential reason behind allowing the execution of a SQL Server procedure inside the function.
Read more »
Learn SQL: SQL Server Cursors
June 22, 2020SQL Server cursors are one common topic on the Internet. You’ll find different opinions when to use them and when not to do it. Today, we’ll also talk about them and answer the question when (not) to use them.
Read more »
Developing your SQL Server database using Azure Data Studio
June 22, 2020In the previous article, Starting your journey with Azure Data Studio, we put the first stone that helps you to be familiar with the Azure Data Studio and start using it to interact with your database objects.
Read more »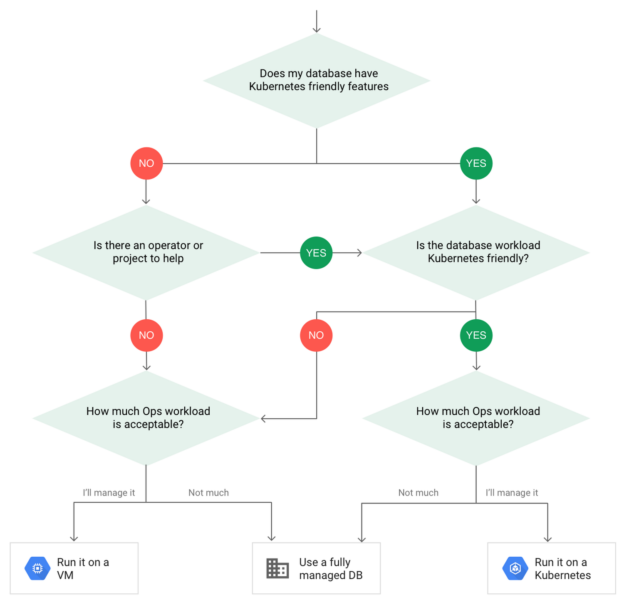
SQL Database on Kubernetes: Considerations and Best Practices
June 22, 2020Database administrators can leverage the scalability, automation, and flexibility of Kubernetes to create a highly available SQL database cluster. In this article, you will learn what Kubernetes is, what are the benefits of running an SQL database on Kubernetes, and how to deploy MySQL on Kubernetes.
Read more »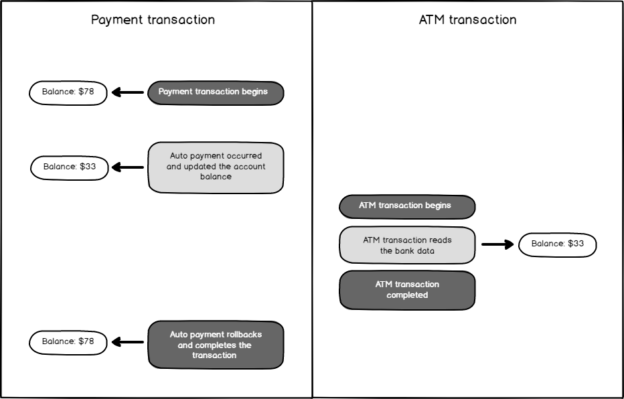
Dirty Reads and the Read Uncommitted Isolation Level
June 22, 2020In this article, we will discuss the Dirty Read concurrency issue and also learn the details of the Read Uncommitted Isolation Level.
Read more »
Security Testing with extreme data volume ranges
June 19, 2020When we develop security testing within inconsistent data volume situations, we should consider our use of anti-malware applications that use behavioral analysis. Many of these applications are designed to catch and flag unusual behavior. This may help prevent attacks, but it may also cause ETL flows to be disrupted, potentially disrupting our customers or clients. While we may have a consistent flow of data throughout a time period – allowing for a normal window of behavior to occur – we may also have an inconsistent data schedule or inconsistent amount of data that cause these applications to flag files, directories, or the process itself.
Read more »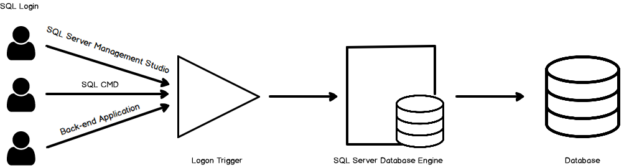
An overview of Logon triggers in SQL Server
June 19, 2020This article gives you an overview of Logon triggers in SQL Server and its usage to control SQL Server authentication.
Read more »